Hacking MFA
Hacking MFA — Defensive Overview Only
Multi-Factor Authentication (MFA) is strong, but attackers try to exploit the human or implementation weaknesses around it.
🛑 1. MFA Fatigue Attacks (Push Bombing)
Attackers send many MFA push notifications hoping the user clicks “Approve” out of annoyance or confusion.
Defense
- Enable number matching
- Limit push attempts
- Use FIDO2 keys instead of push MFA
🛑 2. Social Engineering (Phishing)
Attackers trick users into entering MFA codes on fake login pages.
Defense
- Use phishing-resistant MFA (FIDO2/WebAuthn)
- Train users to identify fake login portals
- Enable conditional access
🛑 3. SIM Swapping
Attackers trick a telecom provider into transferring your phone number to a new SIM card.
Defense
- Avoid SMS-based MFA
- Add a PIN/lock to your mobile carrier account
- Use authentication apps or hardware keys
🛑 4. Session Token Theft
Malware or web exploits can steal an active session token after the user logs in.
Defense
- Use device compliance checks
- Enable continuous access evaluation
- Use secure browsers & EDR tools
🛑 5. Man-in-the-Middle (MitM) Proxy Attacks
Tools like reverse proxies capture usernames, passwords, and MFA codes.
Defense
- Use FIDO2 keys / Passkeys
- Enable TLS 1.2+, HSTS, and certificate pinning
- Implement phishing-resistant Conditional Access
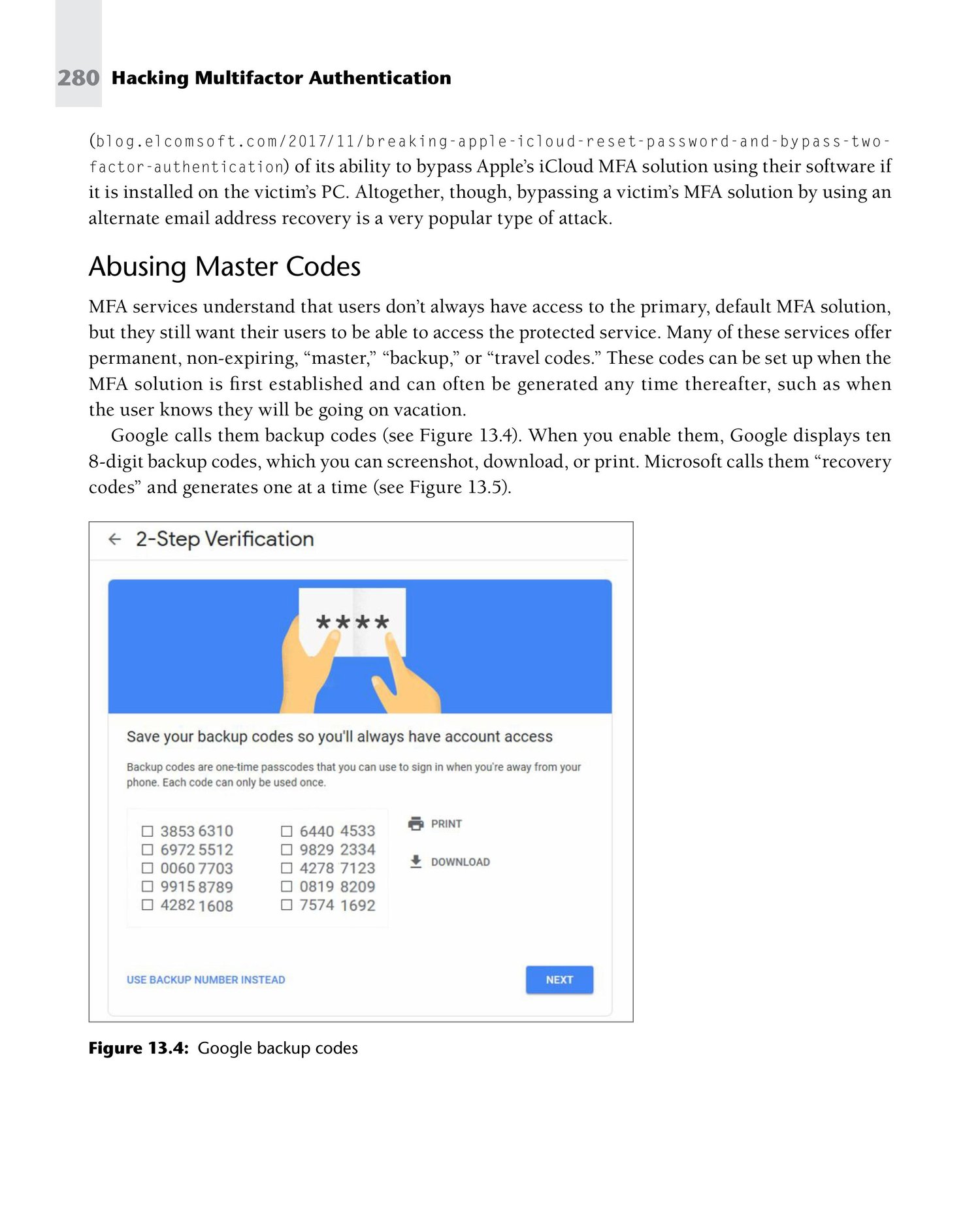
🛑 6. Backup Codes Misuse
Weak backup code security can bypass MFA.
Defense
- Store backup codes in encrypted vaults
- Rotate them regularly
- Disable unused MFA methods
🛡️ Best Practices to Secure MFA
✔ Prefer FIDO2 / Passkeys
✔ Disable weak MFA options (SMS, email OTP)
✔ Enforce Conditional Access Policies
✔ Monitor for impossible travel alerts
✔ Enable Identity Protection (Azure AD / AWS IAM)
✔ Use MFA fraud alert buttons (Reject + Report)
#MFASecurity #IdentityProtection #CyberSecurity #ZeroTrust
#IdentityAndAccessManagement #IAM #EthicalHacking #InfoSec
#AccessControl #SecurityAwareness #CloudSecurity #SOC #BlueTeam
#AccountTakeoverProtection #PhishingDefense #SecurityBestPractices
#DefensiveSecurity #CyberThreats #AuthSecurity #MultiFactorAuthentication